Best Practice 4
These are my recommandations concerning the usage of the azurerm_template_deployment Terraform resource :
- Don’t use the
azurerm_template_deploymentTerraform resource - If you don’t have the choice because one Terraform resource doesn’t exist
- Create a feature request here on GitHub
- Use the
azurerm_template_deploymentTerraform resource (a demo will be shown in this article)
“Terraform can only manage the deployment of the ARM Template - and not any resources which are created by it. It’s highly recommended using the Native Resources where possible instead rather than an ARM Template” (see this article from terraform.io website for more information).
In this article we will perform the following action with :
- Create a Standard Public Load Balancer with outbound rules
- Microsoft associated documentation : Azure Load balancer outbound rules overview
- Azure Rm Template : azuredeploy.json
Prerequisite
| Item | Description |
|---|---|
| Azure Subscription | An Azure subscription id |
| Resource Group | An Azure resource group is available |
| Storage Account | An Azure storage account is available and is located in the upper resource group, it contains a container named tfstate |
| Service Principal | An Azure service principal is available and has the owner privilege on the upper resource group |
| Terraform file | Clone this repository and fill in the following files with the upper prerequisite items : Variable used for the Terraform init : secret/backend-jdld.json Variable used for the Terraform plan and apply : main.tf & main-jdld.tfvars & secret/main-jdld.json |
What should we do?
We will create the upper mentioned element using remote backend (see the previous article BestPractice-1 for more information about remote backend).
Review the main.tf file of the module here. As illustrated in the following bracket that’s how we can push parameters into an AzureRm template (this file template is located here : azuredeploy.json
resource "azurerm_template_deployment" "lb_to_addOutboundRule" {
name = "${var.lbs_out[0]["suffix_name"]}-bck-DEP"
resource_group_name = var.lb_out_resource_group_name
template_body = file(
"${path.module}/AzureRmLoadBalancerOutboundRules_template.json",
)
deployment_mode = "Incremental"
parameters = {
lbName = "${var.lb_out_prefix}${var.lbs_out[0]["suffix_name"]}${var.lb_out_suffix}"
tags = jsonencode(var.lbs_tags)
sku = var.lbs_out[0]["sku"]
allocatedOutboundPorts = var.lbs_out[0]["allocatedOutboundPorts"]
idleTimeoutInMinutes = var.lbs_out[0]["idleTimeoutInMinutes"]
enableTcpReset = var.lbs_out[0]["enableTcpReset"]
protocol = var.lbs_out[0]["protocol"]
lb_public_ip_id = var.lb_public_ip_id
}
}
1. Usage
This step ensures that Terraform has all the prerequisites to build your template in Azure.
terraform init -backend-config="secret/backend-jdld.json" -reconfigure
The Terraform plan command is used to create an execution plan. This step compares the requested resources to the state information saved by Terraform and then gives as an output the planned execution. Resources are not created in Azure.
terraform plan -var-file="secret/main-jdld.json" -var-file="variable/main-jdld.tfvars"
If all is ok with the proposal you can now apply the configuration.
terraform apply -var-file="secret/main-jdld.json" -var-file="variable/main-jdld.tfvars"
We will now destroy what we have done and you will see that our load balancer will not be deleted.
terraform destroy -var-file="secret/main-jdld.json" -var-file="variable/main-jdld.tfvars"
2. Analysis
| Description | Screenshot |
|---|---|
| Have a look on the deployment on Azure | 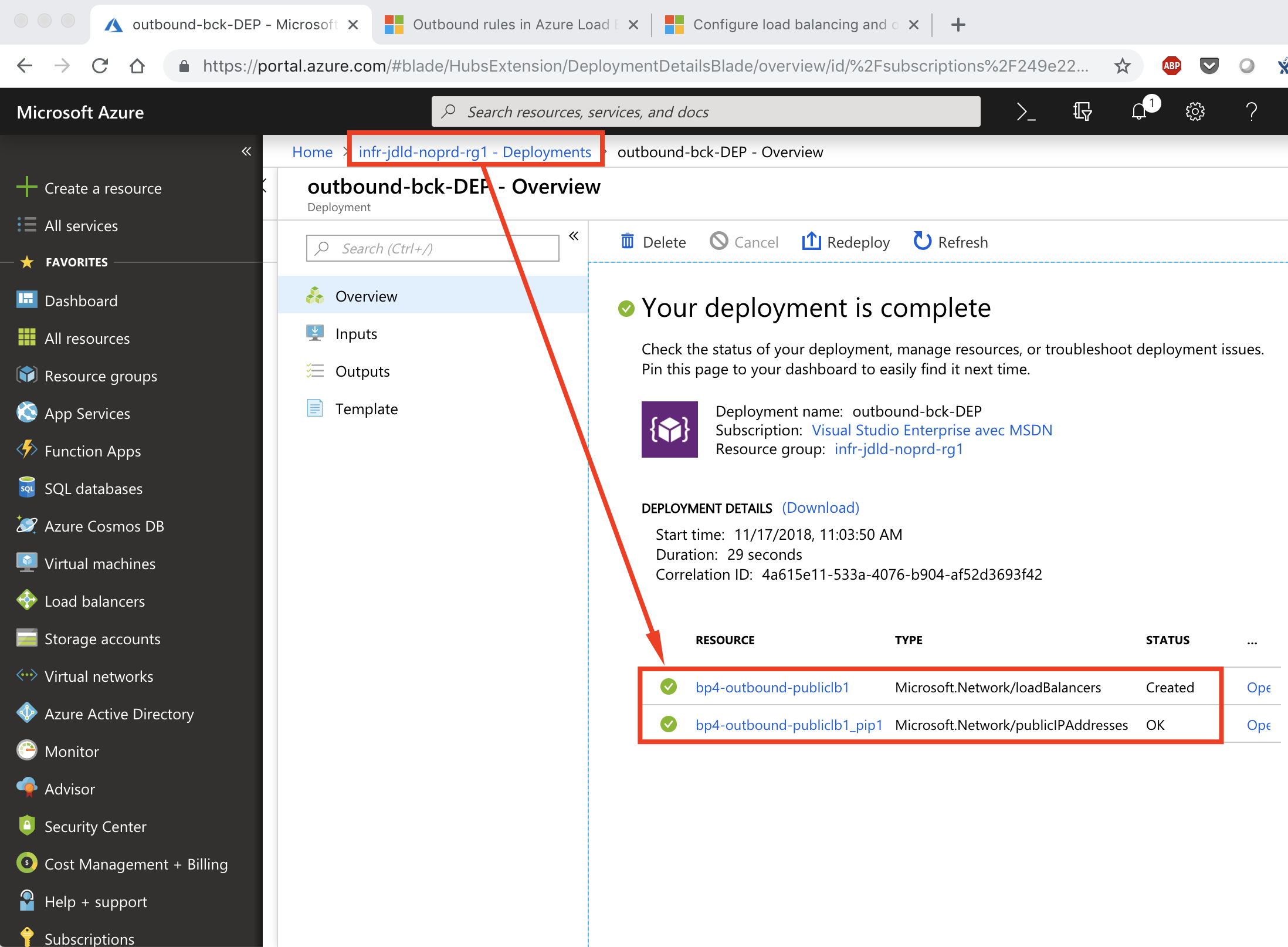 |
When processing a Terraform destroy our deployment object is being deleted |
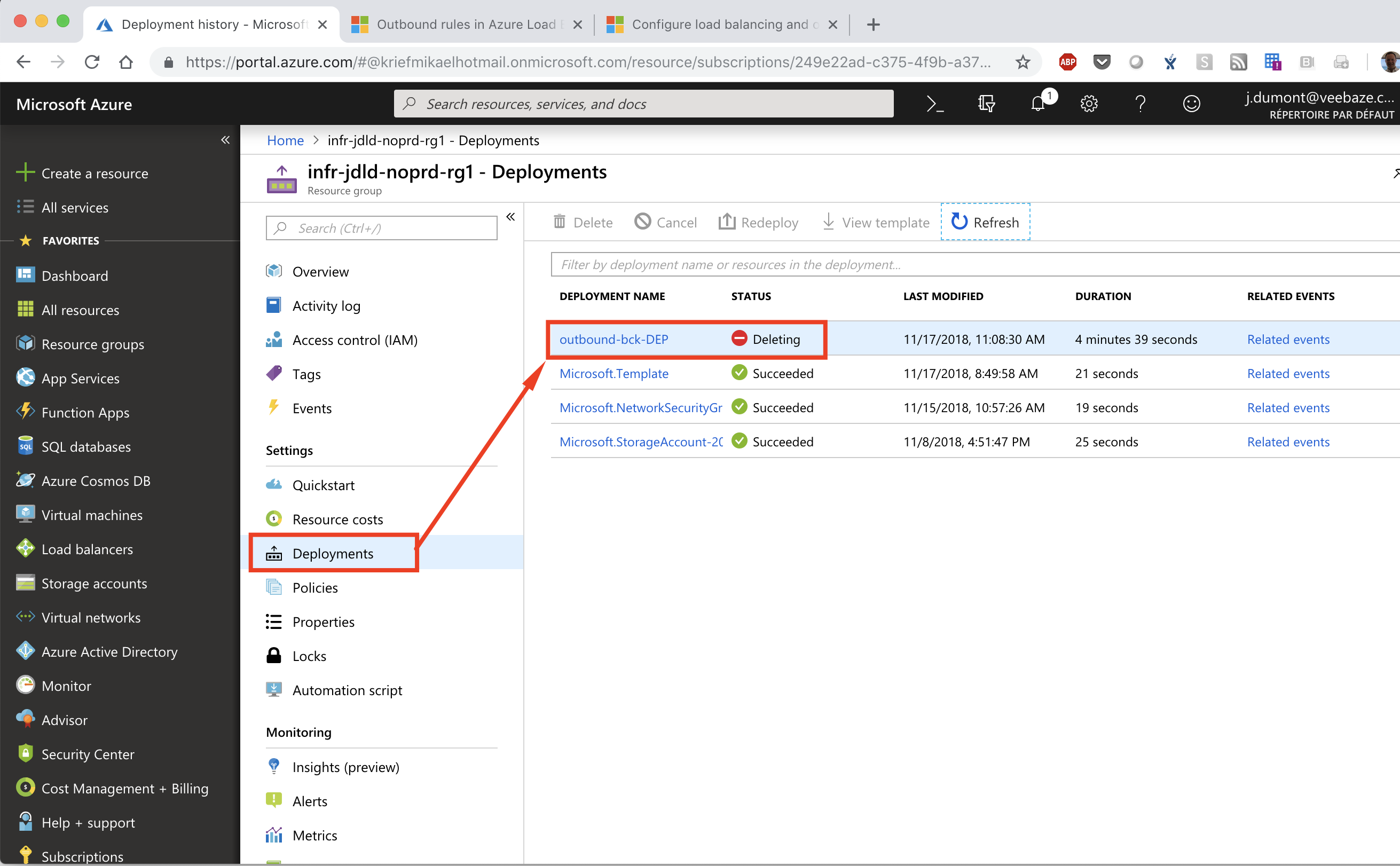 |
After processing a Terraform destroy our load balancer is still available in Azure |
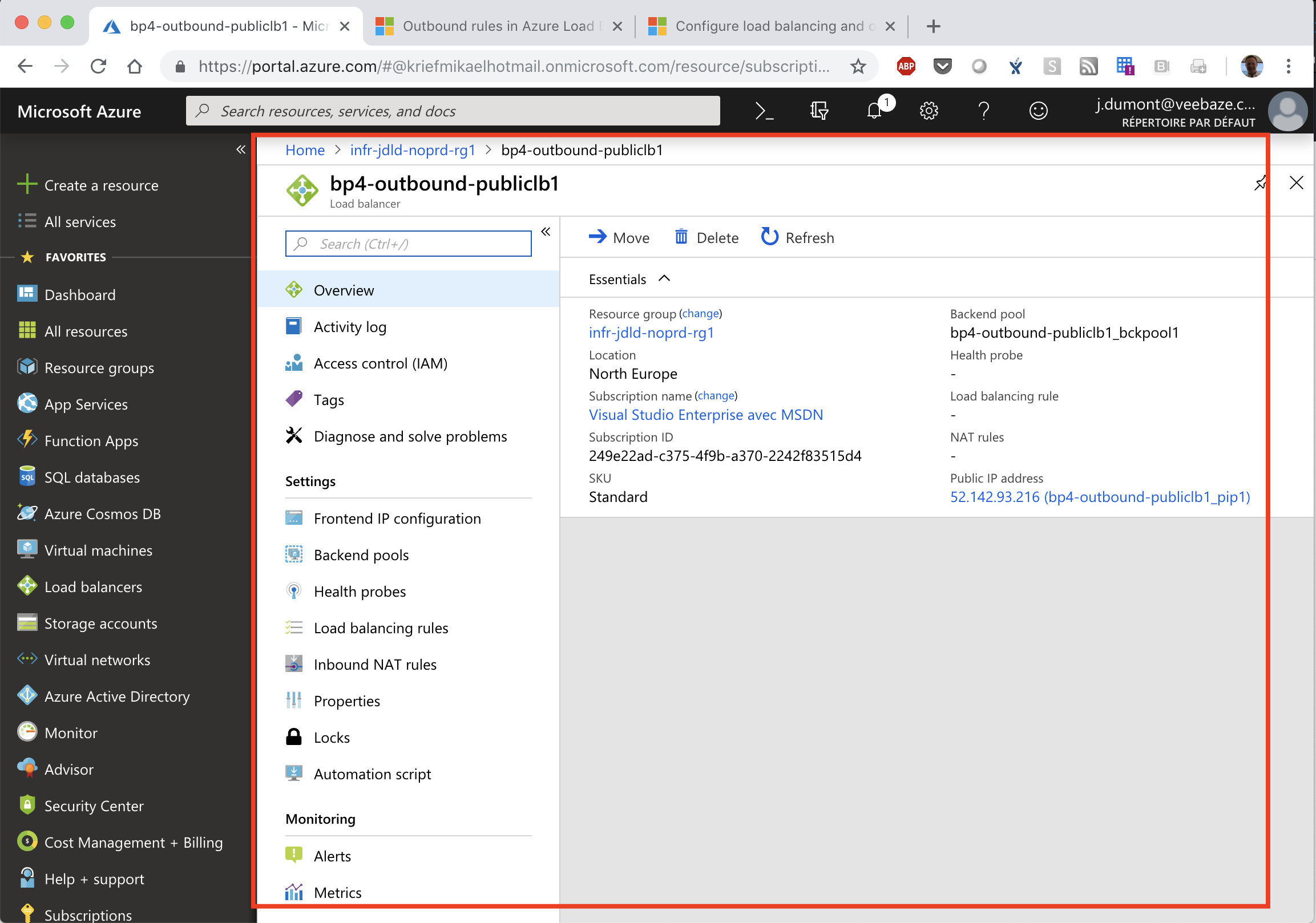 |
See you!
JamesDLD